Top SOC Analyst interview questions and answers in 2024

find references to support your answers, aiding in your preparation. This format is designed to help you concentrate on the essentials for your SOC analyst interview. Explore each category, leverage the provided references, and equip yourself to make a strong impression in your interview.
Top Interview questions and answers for a SOC Analyst role
Fundamental Concepts
1. What is the CIA triad?
The CIA triad refers to confidentiality, integrity, and availability, describing a model designed to guide policies for information security (infosec) within an organization. Confidentiality involves limiting access to data to prevent unauthorized access, integrity ensures the data's trustworthiness and accuracy, and availability aims for reliable access to information by authorized users. These principles are foundational in cybersecurity, guiding the development of security policies and evaluating new technologies. [TechTarget]
2. What is defense-in-depth? or What does a 'layered' approach to security mean?
Defense-in-depth is an information security strategy that integrates people, technology, and operational capabilities to establish various barriers across multiple layers and dimensions of an organization. This approach involves applying multiple countermeasures in a layered manner to achieve security objectives, ensuring that if one layer fails to stop an attack, others will provide additional protection. [NIST]
Read also: What is a Cyber Range?
3. What's the difference between hashing, encoding, and encryption?
Encoding: transforms data from one format to another for interoperability with no security intent; it's reversible using public algorithms.
Encryption: makes data unreadable to unauthorized users, ensuring confidentiality with reversible, key-based algorithms.
Hashing: generates an irreversible fixed-length string unique to the input data. It's mostly used to ensure data integrity by comparing the result with the known valid hash. [Auth0]
4. What is the difference between asymmetric and symmetric encryption?
Symmetric Key Encryption: the same key is used to encrypt and decrypt the messages. This makes it easy to use but less secure. It also requires a safe method to transfer the key from one party to another.
Asymmetric Key Encryption: uses different keys for the encryption and decryption processes. One party can encrypt messages using a known "public" key but only those with the "private" key can decrypt them. It is more secure than the symmetric key encryption technique but is much slower. [GeeksforGeeks]
Read also: SOC Analyst Training and Certifications
5. Explain the concept of zero trust.
The main concept behind the zero trust security model is "never trust, always verify", which means that users and devices should not be trusted by default. This requires continuous verification of their legitimacy before granting access. This model uses robust identity verification, device compliance validation, and least privilege access to enhance security across IT systems. It's designed to adapt to modern corporate networks' complex and interconnected nature, including cloud services, remote environments, and IoT devices. [Wikipedia]
Network Security - Essential SOC Analyst Interview Questions
1. What is a TCP handshake?
A mechanism is designed so that two computers that want to pass information back and forth to each other can negotiate the parameters of the connection before transmitting data such as HTTP browser requests. It involves three crucial steps: SYN, SYN-ACK, and ACK.
Initially, the client sends a SYN (synchronize) packet to the server, requesting a connection. The server responds with a SYN-ACK (synchronize-acknowledge) packet, indicating readiness to establish the connection. Finally, the client sends an ACK (acknowledge) packet back to the server, completing the handshake and establishing a reliable, sequenced, and error-checked channel for data exchange between the two systems. [mdn web docs]
Read also: DFIR Training: Full Guide To Learn Digital Forensics And Incident Response
2. What’s the difference between TCP and UDP?
- TCP (Transmission Control Protocol):
- Connection-oriented: establishes a connection before data transfer.
- Reliable: ensures data delivery in the correct order and resends lost packets.
- Slower due to overhead: ideal for applications where accuracy is crucial, like web browsing and email.
- UDP (User Datagram Protocol):
- Connectionless: sends data without establishing a connection.
- Unreliable: does not guarantee delivery or order, no mechanism for resending lost packets.
- Faster with less overhead: suitable for real-time applications where speed is preferred over reliability, such as video streaming or gaming. [javatpoint]
3. What is the difference between IDS and IPS?
IDS (Intrusion Detection System) and IPS (Intrusion Prevention System) serve to protect network security. On one hand, IDS passively monitors and analyzes network traffic for suspicious activities, alerting administrators without intervening. IPS, however, actively filters network traffic by using a set of rules to inspect it and block or prevent malicious activities. This proactive approach enables IPS to offer immediate threat mitigation.
Read also: What is a Cyber Range?
4. Difference between HIDS and NIDS
HIDS (Host Intrusion Detection System) monitors and analyzes the activities on the host, looking for suspicious activities. It compares current and past snapshots of the file system to detect changes, indicating potential security breaches.
NIDS (Network Intrusion Detection System) oversees the entire network, identifying malicious or unusual activities across all devices connected to it, and initiates alerts for potential threats. The primary differences lie in their operational scope: HIDS for individual hosts and NIDS for network-wide monitoring. [TutorialsPoint]
5. What is MAC/IP address?
- IP Address: Assigned by network software, it identifies a device globally for internet-based communication. It's flexible and can change with the network environment, facilitating device connectivity across networks.
- MAC Address: Hard-coded into a device's network interface card, it provides a unique identifier for local network activities. It's used for specific device identification and communication within the same network, remaining constant regardless of network changes. [TechTarget]
6. What is network segmentation, and how is it helpful? What is the purpose of sub-netting, and why is it used?
Network segmentation involves dividing a larger network into smaller, manageable subnets. This strategy enhances security by creating boundaries that control traffic flow, limiting access to sensitive information, and reducing the risk of lateral movement by attackers. Additionally, segmentation improves network performance by reducing congestion, facilitating more efficient data routing, and aiding in compliance with regulatory requirements by isolating regulated data. It's a key component in modern network architecture to secure and optimize network resources. [Palo Alto]
7. How would you detect and mitigate a Man-in-the-Middle (MitM) attack in a corporate network?
A man-in-the-middle (MITM) attack involves intercepting communication between two parties for unauthorized information gathering or alteration.
- Detection Methods:
- Monitoring for unexpected disruptions in service.
- Monitoring for unusual SSL/TLS certificate errors
- Employing intrusion detection systems to spot unauthorized interceptions.
- Mitigation Methods:
- Encrypting data in transit using protocols such as HTTPS, SSH, and IPSec to secure data communications.
- Regularly updating and patching software and systems to fix vulnerabilities that could be exploited in MitM attacks.
- Educating employees about the risks of MitM attacks and safe practices, such as not connecting to unsecured public Wi-Fi networks without VPN protection.
Web Application Security
1. How would you detect an attempted directory traversal attack on your network?
Detecting an attempted directory traversal attack involves monitoring and analyzing web application logs for unusual activity, such as requests containing "../", unusual paths that attempt to access unauthorized directories or patterns that deviate from normal user behavior. Implementing file integrity monitoring can also help by alerting when unauthorized changes are made to critical files. Utilizing a Web Application Firewall (WAF) configured to detect and block directory traversal patterns is another effective strategy. Regularly updating and patching web applications and servers to address known vulnerabilities is crucial for prevention.
2. How do you differentiate between a legitimate spike in web traffic and a DDoS attack?
Differentiating between a legitimate spike in web traffic and a DDoS attack involves analyzing the nature and source of the traffic. Look for patterns such as traffic volume that significantly exceeds normal levels, a high number of requests from a single or few IP addresses, or requests that target specific endpoints or resources repetitively. Legitimate spikes often coincide with marketing campaigns or events and show diverse geographic origins and device types. At the same time, DDoS traffic may appear more uniform and lack the behavioral complexity of real users.
3. What is SQL Injection?
SQL Injection is a web security vulnerability that allows attackers to interfere with the queries that an application makes to its database. It lets attackers view data they are not normally able to retrieve, including data belonging to other users or any other data the application can access. In some cases, it allows attackers to modify or delete this data, causing persistent changes to the application's content or behavior.
4. How can you detect it and prevent it?
Closely monitor your web application's logs for unusual or unexpected SQL queries. This involves analyzing URLs, form inputs, and cookies for patterns indicating SQL code injection attempts, such as using SQL syntax like 'OR '1'='1'. Monitor for unusual database errors, unexpected application behavior, and unusual patterns in the SQL queries logged.
Intrusion detection systems can help automate this analysis by alerting on patterns typical of SQL Injection. Additionally, performing regular security audits and vulnerability scans can help identify potential SQL Injection vulnerabilities before they are exploited.
5. Explain the significance of the OWASP Top 10 for web application security and how you would use it in your security practices.
The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications. I integrate its principles into security practices by guiding secure coding practices, and using it as a benchmark for security audits and training programs. This proactive approach ensures robust defense mechanisms against common threats. The image below shows the difference between 2017 and 2021 versions. [OWASP]
6. Discuss WAF's differences and use cases (Web Application Firewall) versus traditional network firewalls.
WAFs (Web Application Firewalls) are designed specifically for monitoring HTTP traffic to and from a web application, providing protection against application-layer attacks such as XSS, SQL injection, and CSRF. Traditional network firewalls, on the other hand, control inbound and outbound traffic based on IP addresses, ports, and protocols, offering a broader network perimeter defense without the granularity to address specific web application vulnerabilities. WAFs are used for targeted application security, while network firewalls serve as the first line of defense against general network threats. [Fortinet]
Log Analysis & SIEM
1. How does a SIEM work? How are they set up?
SIEM tools collect and aggregate data from various sources across an organization's IT infrastructure, including servers, devices, and applications. This data is then analyzed in real-time to identify abnormal behavior that could indicate a security threat. Key components of a SIEM system include:
- Agents: Software installed on devices to collect and send data to the SIEM.
- Collectors: Gather data from various sources, including agents and devices that can't run agents.
- Forwarders: Transfer data to the SIEM system, particularly when collectors are not directly accessible.
- Rule Tuning: Adjusting SIEM rules to reduce false positives and ensure accurate threat detection. [Microsoft]
2. What are indicators of compromise?
Indicators of Compromise (IoCs) are pieces of forensic data that identify potentially malicious activity on a system or network. Examples include unusual network traffic, unexpected changes in file integrity, suspicious registry or system file changes, and anomalies in user account behavior. Security teams use IoCs to detect breaches early, facilitating rapid response to mitigate damage. These indicators are crucial for understanding a security threat's scope and taking appropriate corrective actions. [Trend Micro]
3. Where do you go to find an event in Windows & Linux systems?
In Windows, you can find event logs through the Event Viewer, where system, security, and application-related events are logged. In Linux, events are typically logged in the /var/log directory, with different files for various types of logs, such as syslog for system events and auth.log for authentication events. These tools and directories are essential for system administration, troubleshooting, and security auditing.
4. What is the difference between a security event and a security incident?
A security event is any observable occurrence in a system or network, which can include both normal and potentially harmful activities. A security incident, however, is a subset of security events that indicates a violation of an organization's security policies, standards, or practices, potentially impacting the confidentiality, integrity, or availability of information. Incidents require a response to mitigate damage or recover from the event.
Security Policies and Procedures
1. What is the MITRE ATT&CK framework?
The MITRE ATT&CK framework is a comprehensive knowledge base of adversary tactics and techniques based on real-world observations. It's used to understand attacker behavior, improve cybersecurity posture, and develop strategies to detect, prevent, and mitigate cyber threats effectively. [Mitre]
2. What is an advanced persistent threat (APT), and how might you identify one?
An advanced persistent threat (APT) is a prolonged, targeted cyberattack where an intruder gains access to a network and remains undetected for an extended period. APTs aim to steal data rather than damage the network, typically carried out by well-funded groups targeting high-value entities. Techniques include spear phishing, zero-day exploits, and command-and-control servers, among others. Identifying an APT involves detecting unusual user account activity, unexpected database operations, or spear-phishing attempts, indicating potential unauthorized access or data exfiltration efforts. [TechTarget]
3. What is the difference between a risk, a vulnerability, and a threat?
Vulnerability: A weakness in a system that can be exploited. It’s a specific flaw or deficiency in hardware or software.
Threat: Anything that can exploit a vulnerability, intentionally or accidentally, and obtain, damage, or destroy an asset.
Risk: The potential for loss, damage, or destruction of an asset as a result of a threat exploiting a vulnerability. It considers both the probability of an attack and its potential impact.
4. Explain the differences between blue, red, and purple team activities. How does each contribute to an organization's cybersecurity?
Red teams simulate attackers to identify security weaknesses, while blue teams defend against these simulated attacks. Purple teams enhance collaboration between red and blue teams, integrating offensive and defensive tactics. These activities collectively bolster an organization's cybersecurity by uncovering vulnerabilities, improving defenses, and fostering a culture of continuous security enhancement. [Coursera]
Malware Analysis - SOC Analyst Interview Questions and Answers
1. What is ransomware?
Ransomware is malware that blocks access to a victim's data, often through encryption and demands payment for restoration. It can spread via Trojans, often disguised as legitimate files. Payments are typically demanded in hard-to-trace digital currencies like Bitcoin. The impact of ransomware has grown, with millions of attacks recorded annually, emphasizing the need for robust cybersecurity measures. [Wikipedia]
2. What is a simple way of knowing if a file contains malware?
A simple way to check if a file may contain malware is to use online virus scanning services like VirusTotal. You upload the suspicious file, and it will be scanned using multiple antivirus engines to detect potential malware. Additionally, be cautious with files from unknown sources and keep your antivirus software updated for real-time protection. For more detailed techniques and tools, visiting cybersecurity websites can provide further insights.
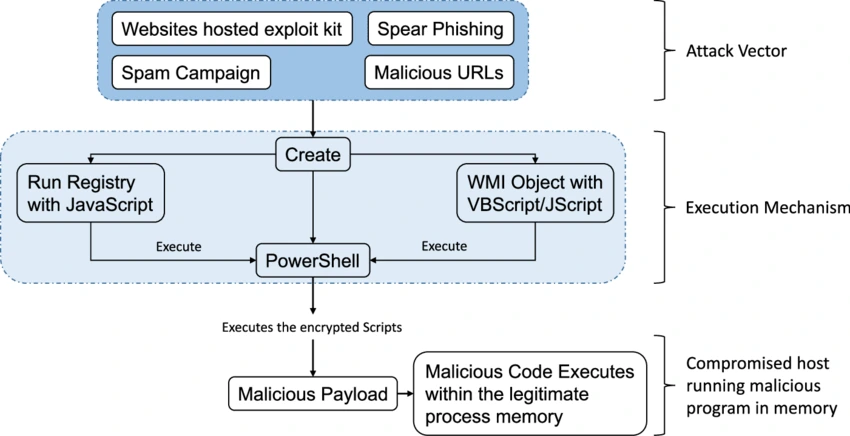
3. What is fileless malware, and why is it challenging to detect? How would you mitigate the risks associated with it?
Fileless malware leverages legitimate system tools to execute attacks, making it difficult to detect since it doesn't rely on files to operate. It can exploit system vulnerabilities, modify registry keys for persistence, or execute directly in memory. Mitigation includes employing advanced security measures like behavioral detection, restricting the use of scripting environments like PowerShell, and regular system patching. [CrowdStrike]
4. Give me an example of a ransomware incident that piqued your interest. And why?
One of the most significant ransomware attacks in 2023 involved the Lehigh Valley Health Network, where the BlackCat ransomware group attacked, affecting sensitive patient data, including radiation oncology treatment images. The attackers demanded a ransom, which LVHN refused to pay, leading BlackCat to leak sensitive images to increase pressure. This incident highlights the evolving extortion tactics of ransomware groups and the vulnerability of healthcare organizations to such attacks. [TechTarget]