
You'd be mistaken if you thought cyber security is just about hacking into organizations; it's also about actively testing for vulnerabilities and strengthening an organization's defenses. This is where the concept of red team vs. blue team comes into play. According to the IBM Cost of a Data Breach Report, the average cost of a data breach in 2023 was $4.45 million, so there's no better time than now to enter the cybersecurity field. In this article, we'll explore the roles, responsibilities, and skillsets of blue teams vs. red teams and how they work together to strengthen an organization's security posture.
Make an informed decision; keep reading to uncover the unique challenges and opportunities that await you on either side.
What is a Blue Team?
According to the SANS Institute glossary, a blue team is the people who perform defensive cybersecurity tasks, including placing and configuring firewalls, implementing patching programs, enforcing strong authentication, ensuring physical security measures are adequate, and a long list of similar undertakings. In simpler terms, they are the first line of defense, working to protect the organization's assets, data, and systems from unauthorized access or damage.
Key Roles and Responsibilities of a Blue Teamer:
- Managing security tools
- Developing and maintaining incident response plans and procedures
- Monitoring the logs of all endpoints and services
- Responding to security incidents in case of an attack
The Blue Team Skillset
Members of the blue team should have a variety of skills in order to be successful:
- They must be well-versed in incident response, possess a solid foundation in cybersecurity principles, and be proficient with a variety of security tools.
- It is essential to have analytical and problem-solving abilities as well as the ability to think from an attacker's point of view.
- Working with IT teams and management effectively requires excellent communication and teamwork skills.
- Success in this position requires a dedication to lifelong learning, obtaining practical certifications, and keeping up with emerging developments in cybersecurity.
Read also: SOC Analyst Training and Certifications
What is a Red Team?
Red teams approach cybersecurity offensively, in contrast to blue teams' defensive strategy. A Red Team is a collection of individuals authorized and coordinated to simulate an adversary's attack or exploitation capabilities against an enterprise's security posture, according to the National Institute of Standards and Technology (NIST). Simply put, they attempt to obtain unauthorized access to the organization's systems by acting and thinking like malicious attackers looking to penetrate the organization's defenses.
Key Roles and Responsibilities of a Red Teamer:
- Carrying out penetration tests
- Demonstrate vulnerability exploitation in networks, applications, and systems
- Managing phishing and social engineering campaigns
- Providing thorough reports on results
The Red Team Skillset
Members of the red team should have a variety of skills in order to be successful:
- They have to have in-depth knowledge of offensive security methods, tools, and techniques. Combined with a creative mindset to come up with novel methods to breach defenses and exploit vulnerabilities.
- Outstanding analytical and problem-solving skills to come up with successful attack plans, handle complicated security systems, and adjust to changing defenses.
- Ability to clearly communicate findings, recommendations, and the possible impact of vulnerabilities found to both technical and non-technical stakeholders through report writing.
- Maintaining a competitive edge through a dedication to lifelong learning, remaining on top of security research, emerging technologies, and hacking techniques.
Read also: DFIR Training: Full Guide To Learn Digital Forensics And Incident Response
Blue Team VS. Red Team Exercises
Red team/blue team exercises involve real-world simulated attacks in a controlled setting. The red team should try to breach defenses by techniques such as social engineering, exploiting vulnerabilities, and gaining unauthorized physical access. In contrast, the blue team should concentrate on detection, investigation, and response. The exercises should assess the effectiveness of security controls, incident response procedures, and defender skills.
To enhance value, the red team should have specific objectives to achieve that resemble genuine adversaries. To ensure a proper assessment, the blue team should actively work to detect, contain, and repel simulated attacks. Following the exercise, communication and information exchange among teams is critical for analyzing results, identifying gaps, and implementing adjustments to boost the organization's overall security posture.
But what if there was a simpler and more efficient approach to assessing an organization's security posture? Introducing purple teams.
Read also: Top SOC Analyst interview questions and answers in 2024
What is a Purple Team?
"Combining elements of offensive and defensive cybersecurity, a purple team approach is a cooperative method of threat mitigation. The name""purple" refers to combining the red and blue teams in order to strengthen the overall security posture of an organization."Combining elements of offensive and defensive cybersecurity, a purple team approach is a cooperative method of threat mitigation. The name "purple" refers to combining the red and blue teams in order to strengthen the overall security posture of an organization.
A purple team's main goal is to help the offensive and defensive teams communicate, share knowledge, and always strive for improvement. Organizations can optimize their cybersecurity operations by merging the defensive strategies of the blue team with the adversarial mindset of the red team. Purple teaming is essentially a collaborative effort that supports organizations in identifying and addressing vulnerabilities more quickly.
Key Roles and Responsibilities of a purple teamer:
- Encouraging cooperation and information exchange between the red and blue teams
- Developing and carrying out practical attack scenarios to evaluate defenses
- Evaluating incident response protocols and security controls
- Presenting recommendations based on findings for enhancing the overall security posture
Organizations can gain various benefits from building a purple team, such as:
- Enhanced cooperation and exchange of information between the red and blue teams
- More thorough and realistic testing of incident response protocols and security controls
- Quicker vulnerability and security gap identification and resolution
- Improved alignment of risk management techniques and corporate objectives with cybersecurity activities
Read also: What is a Cyber Range?
Blue Team vs. Red Team vs. Purple Team
The following table summarizes the differences between the different cybersecurity teams.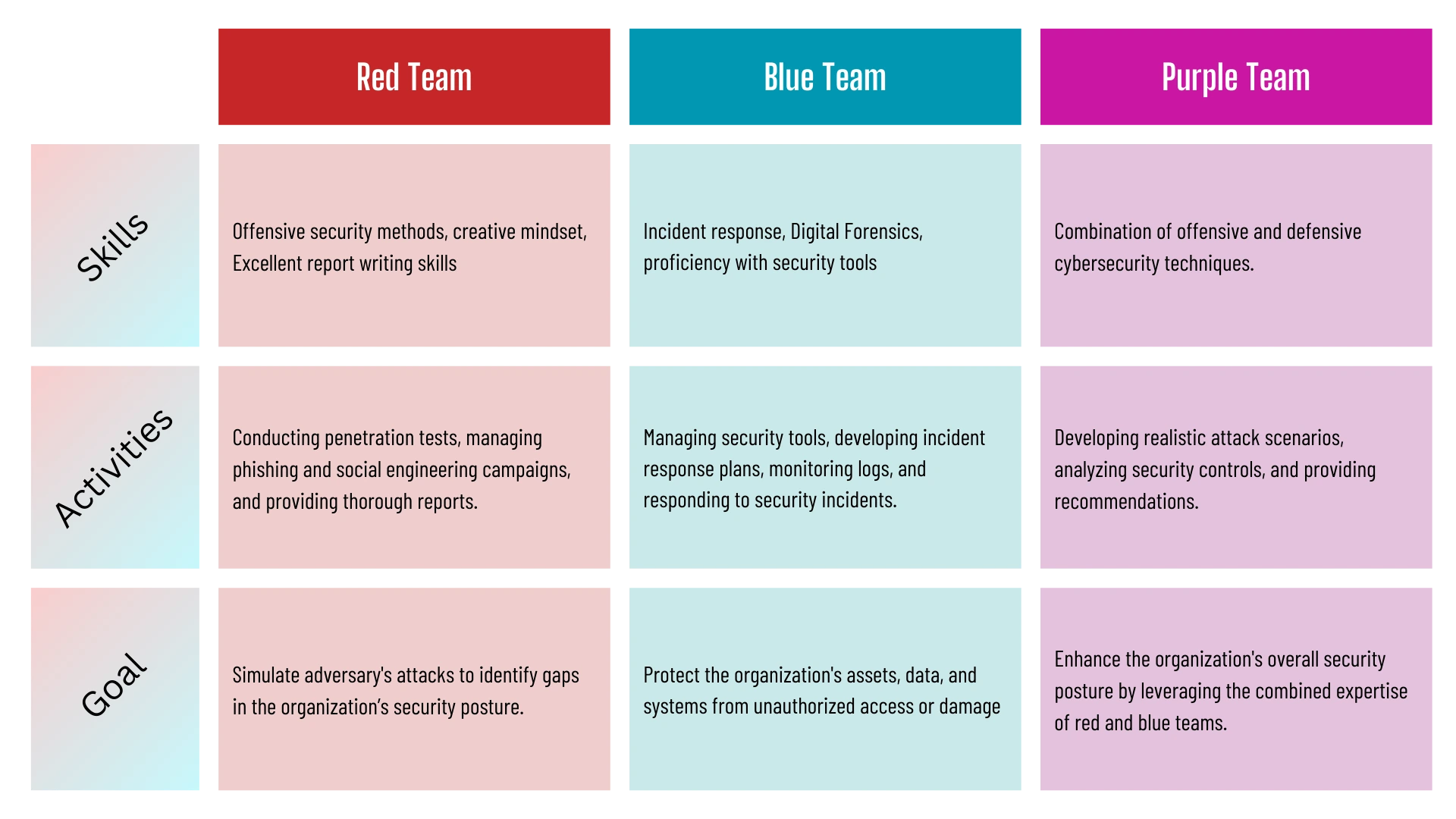
Take your next step
It's time to move on to the next phase of your journey now that you are aware of the crucial roles that red teams and blue teams play in cybersecurity. There are plenty of chances to truly leave an impact in this fast-paced industry, regardless of whether you're drawn to the analytical mindset of blue teaming or the creative problem-solving of red teaming. Begin by exploring online resources, attending cybersecurity conferences, and networking with industry professionals. As your knowledge and abilities grow, look into getting the necessary certifications to demonstrate your proficiency. Seize the chance to start a fulfilling career that changes the world and enter the exciting field of cyber security.
References:
IBM: IBM Cost of a Data Breach Report
SANS Institute: https://www.sans.org/security-resources/glossary-of-terms/
Blue team(computer security): https://en.wikipedia.org/wiki/Blue_team_(computer_security)
Rapid7: https://www.rapid7.com/blog/post/2023/08/31/pentales-what-its-like-on-the-red-team/
NIST Glossary: https://csrc.nist.gov/glossary/term/red_team
INE: https://ine.com/blog/understanding-purple-team-roles
CrowdStrike: https://www.crowdstrike.com/cybersecurity-101/purple-teaming/
