Introduction
Manuel, an enthusiastic gamer, recently installed popular Minecraft resource packs on his new computer after classmates shared download links with him. Soon after, he noticed system slowdowns, unexpected pop-ups, and malfunctioning applications. You have been asked to investigate how a suspicious file infiltrated the machine, whether it created hidden persistence mechanisms, and assess any impact on personal data or overall system stability.
Analysis
Q1) The threat actor has set up a video to provide the link that hosts the filefix command file. What is the YouTube channel display name of the threat actor?
To determine the YouTube channel used by the threat actor to host the malicious video containing the filefix command link, we begin by identifying user activity on the compromised system. Disk forensics reveals a local user account named "admin," which shows signs of recent interaction. We pivot to browser artifacts to reconstruct the user’s web activity, as malicious links are often delivered via video platforms.
The admin user primarily utilized Microsoft Edge. Let's navigate to the Edge history database on the disk image:
C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\History
Using DB Browser for SQLite, we open the History file and examine the "urls" table, which logs visited sites with timestamps and titles.
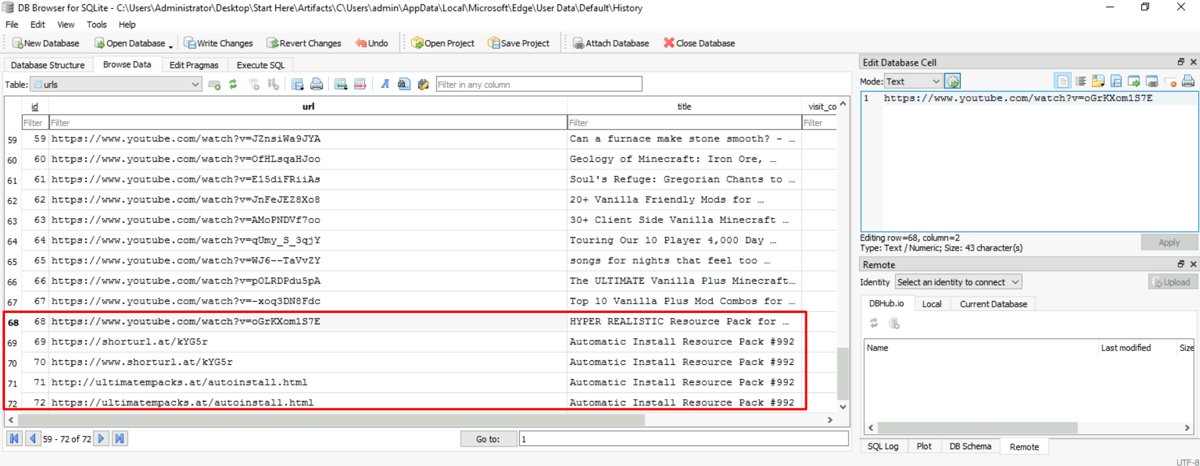
Querying the table reveals a pattern of consistent YouTube video consumption. Amid this activity, a sudden deviation appears: the user accessed a shortened URL, https://www.shorturl.a
Unlock Your Full Learning Experience with BlueYard Labs
Sign up to track your progress, unlock exclusive labs, and showcaseyour achievements—begin your journey now! Join for Free