Introduction
In this lab, an IcedID malware sample is analyzed to investigate the activities of an advanced persistent threat (APT) group responsible for widespread phishing campaigns. These campaigns are used to distribute malicious payloads, including IcedID, to compromise systems. The primary tools utilized in this lab include VirusTotal for file examination, Malpedia for malware classification, and social media platforms like Twitter for gathering threat intelligence. Practical skills in malware analysis, threat actor identification, and understanding the mechanisms by which IcedID operates are developed. By the end of this lab, essential cybersecurity techniques for tracking, analyzing, and mitigating malware threats will have been practiced and refined.
Analysis
Q1: What is the name of the file associated with the given hash?
The hash provided, 191eda0c539d284b29efe556abb05cd75a9077a0, is submitted to VirusTotal for analysis.
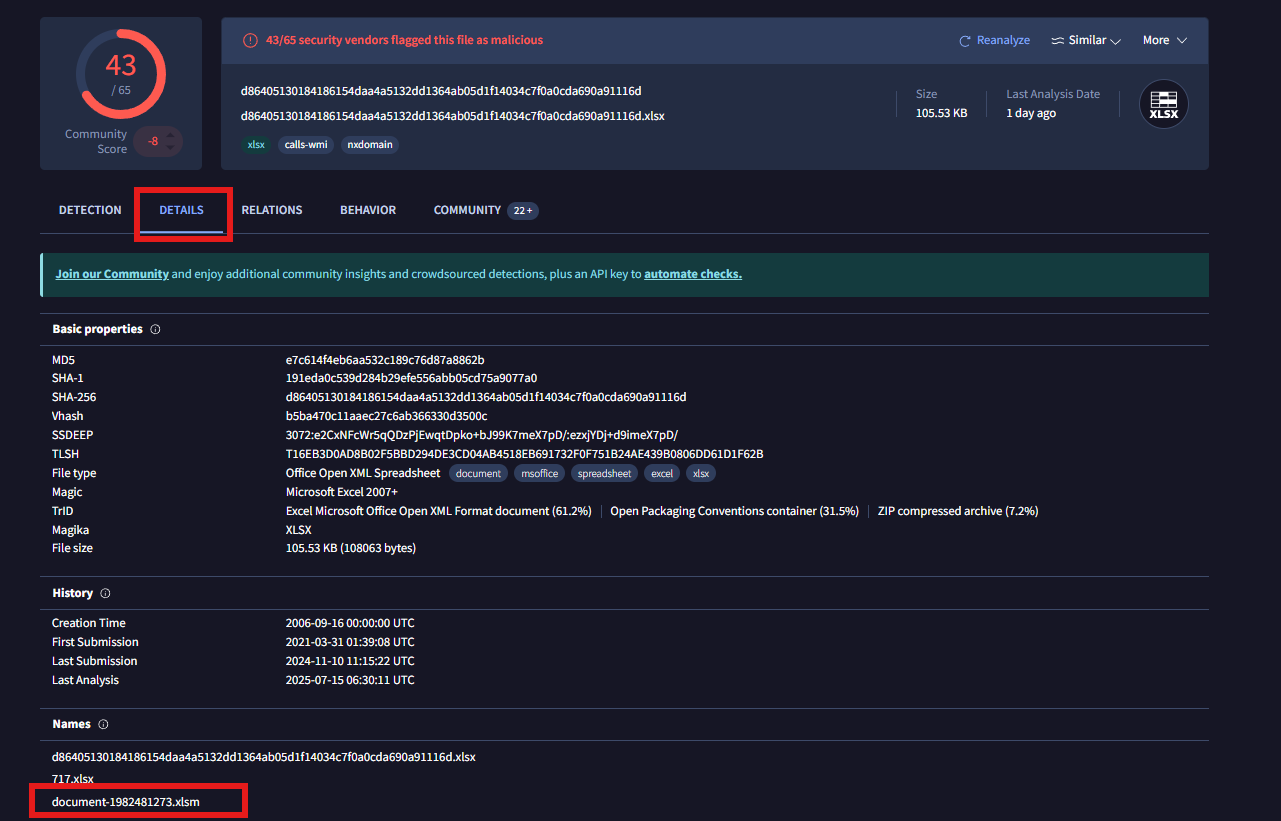
In the Details section, the original filename is located. The file, identified as document-1982481273.xlsm, is determined to be an Excel macro-enabled workbook. Files of this type are commonly exploited by threat actors to execute malicious macros upon opening, facilitating the initial stage of
Unlock Your Full Learning Experience with BlueYard Labs
Sign up to track your progress, unlock exclusive labs, and showcaseyour achievements—begin your journey now! Join for Free